As of January 16, 2023, the European Network and Information Security Directive (NIS2) was published. With the goal of enhancing Europe’s cybersecurity and protection against threats, NIS2 comes with stricter rules and wider scope of measures applicable to a much larger pool of industries. But what are the real implications of NIS2, compared to its predecessor NIS1, and how will NIS2 affect the aviation industry?
Key differences between NIS1 and NIS2.
Wider scope means it affects more organisations, including your supply chain.
NIS2 applies to a much larger group of entities compared to NIS1. Where NIS1 primarily applied to operators of essential infrastructures such as energy providers or airports, NIS2 takes the next step, widening the overall scope of entities required to comply with the newly enacted legislation – to include suppliers for example. Under NIS2, harmonised rules are introduced for medium sized and large entities (and key providers to those critical entities), categorized as either “important” or “essential”. Whether an organization is labelled as essential or important depends on whether the organization falls under a critical or a very critical sector and depends on the size of the company, and its potential impact to the state and European economy.

One of the key areas of the NIS2 Directive are requirements for assessing supply chain security. One of the responsibilities of essential and important entities will be to implement appropriate and proportionate technical, operational and organizational measures to ensure supply chain security. The regulation requires member states to ensure that entities covered under NIS2 “take into account the vulnerabilities specific to each direct supplier and service provider and the overall quality of products and cybersecurity practices of their suppliers and service providers, including their secure development procedures. Member States shall also ensure that, when considering which measures referred to in that point are appropriate, entities are required to take into account the results of the coordinated security risk assessments of critical supply chains carried out in accordance with Article 22(1).”
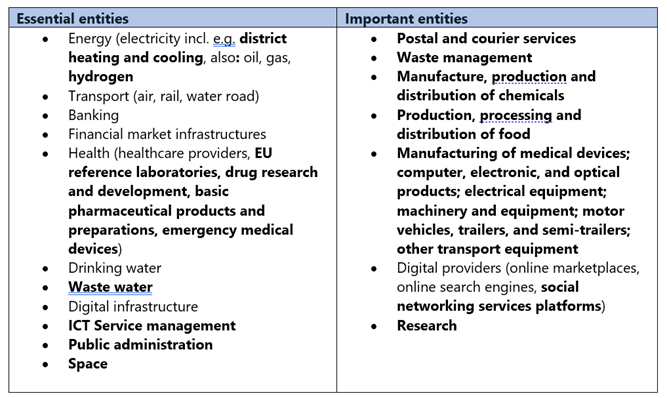
New sectors and services that are now within scope include manufacturers of chemicals, medical devices, digital providers of social platforms, but also industries like space or activities such as public administration. Both essential and important entities are subject to the same cybersecurity management and reporting requirements, with the only difference being in the enforcement and penalty fee structure. The table below provides a better picture of entities that now fall under NIS2, with new additions highlighted in bold.
Requirements extended to include new policies and training.
As well as wider scope, the NIS2 legislation also brings more complex requirements than NIS1. It directly addresses the management of the entities in scope with new governance and accountability obligations. The management board must approve the cybersecurity risk-management measures taken, oversee its implementation and can be held liable if they fail to comply with security obligations. In addition, NIS2 requires them to take training to gain the skills needed to identify risks and assess cybersecurity risk-management practices and the impact on the services they provide.
Another requirement is a minimum set of technical and organisational measures that all organisations in scope will need to implement. These include for example policies on risk management, information system security, backups, incident response, cryptography, multi-factor authentication, and many other areas.
No hiding place under stricter reporting rules.
The reporting obligations originally set by NIS1 are also expanded upon under NIS2. Any significant cyber incident must be reported within 24 hours to the member state’s computer security incident response teams or the relevant supervisory authority, something that was not as strictly required by the previous legislation. The significance of an incident (and hence the appropriate action to be taken) is determined by considering the wider impact, with criteria such as severe operational disruption of the organisation’s services, economic loss, or by the undermining of other protections against damage or further disruption. As a result, there is a greater expectation for states to work together and with a pan-European cyber coordination entity.
One major reporting change under NIS2 is the need to notify other parties of significant incidents that are likely to affect the provision of specific services. Similar to the General Data Protection Regulation (“GDPR”) where an organization is required to immediately inform other parties when a cyber incident occurs, organizations in scope of NIS2 are no longer allowed to hide the existence of significant incidents.
Enforcement remains the responsibility of EU member states.
Enforcement of the newly defined rules is a key factor in the overall NIS 2 compliance process. With NIS2 being an EU based legislation, member states are ultimately responsible for ensuring that competent authorities (i.e. state-wide authorities and institutions) supervise and take the measures necessary to ensure compliance with the legislation. The supervisory function could range anywhere from the authority performing security audits, inspections, accessing data, or simply requesting specific information or evidence. When enforcement measures are ineffective, supervisory authorities can use follow-up measures, potentially resulting in the suspension of a certification or even more stringent, costly measures. This can include fines up to EUR 10 million or 2% of annual global turnover for essential entities and EUR 7 million or 1.4% of annual global turnover for important entities.
What we also notice here is a mindset shift in approaching cybersecurity. Where NIS1 used very much a reactive approach, emphasizing preventive measures to improve cybersecurity, NIS2 takes a different, more proactive approach through enforcement of the defined rules, and also the Compromise Amendment 1 (amendment to the legislation) that lays down enforcement obligations on member states.
